Overview of No Code Flows
EmpowerID's No Code Flows provides a way to automate complex business processes without the need for traditional coding. This system helps administrators design, manage, and enhance intricate workflows securely and efficiently. The system has a component-based architecture with predefined elements to connect different stages of a business process. This approach eliminates the coding barrier associated with traditional workflow management.
Core Concepts
EmpowerID’s No Code Flows framework is designed to automate business processes by seamlessly integrating Flow Events, Flow Items, Flow Definitions, and Flow Policies. These components work together to define how events are triggered, what actions should be taken, and how workflows are structured and executed. Learn more by clicking each tab below.
- Flow Events
- Flow Items
- Flow Definitions
- Flow Policies
Flow Events are the starting point of any workflow. They act as triggers that initiate a business process. For instance, a Flow Event could be a new employee joining the organization, triggering a series of onboarding tasks.
When an event is triggered, it is directed to the Flow Event Inbox, which holds events until they are processed. Examples of Flow Events include:
- Mailbox Discovered – A new mailbox is detected, requiring actions such as verification, adding it to distribution lists, or configuring access controls.
- Account Takeover – Indicates potential unauthorized access, prompting actions such as account suspension, security team notifications, and further investigation.
- Person Leaver – Triggered when someone leaves the organization, requiring actions like disabling accounts, updating group memberships, and revoking access.
EmpowerID includes several predefined Flow Events. Below is a list of selected Flow Events with descriptions to provide more insight into their functionality.
View Default Flow Events
| Flow Event | Description |
|---|---|
| Primary Business Role Location Changed Automatically | Primary Business Role Location Changed based on Directory Data and RBAC Mappings, by the Role and Location Compiler/Processor Jobs. |
| Secondary Business Role Location Added Automatically | Secondary Business Role Location Added based on Directory Data and RBAC Mappings, by the Role and Location Compiler/Processor Jobs. |
| Primary Business Role Location Reverted TO DEFAULT Automatically | Primary Business Role Location Reverted TO DEFAULT due to lack of Directory Data or RBAC Mappings, by the Role and Location Compiler/Processor Jobs. |
| Person Leaver | Person Termination or Planned Leaver. |
| Person Mover | Person Mover Lifecycle Event. |
| Person Joiner | Person Joiner/Onboard Lifecycle Event. |
| Possible Account Takeover | Possible Account Takeover - possibly an account has been compromised. |
| Mailbox Discovered | New mailbox detected event. |
| Account Inbox Person Provision | Person provisioned from Account Inbox process. |
| Person Inbox Joiner | Person Inbox Joiner. |
| Person Rehire | Rehire Person. |
| Person Reactivation | Cancellation of planned leaver event or Person reactivation after disablement. |
| Person Preleaver Notification | Notification about upcoming leaver event. |
| Secondary Business Role Location Removed Automatically | Secondary Business Role Location Removed based on Directory Data and RBAC Mappings, by the Role and Location Compiler/Processor Jobs. |
Flow Items are the specific tasks or actions performed in response to Flow Events. Each is designed to handle a particular aspect of the event response. For example, if a Person Leaver event is detected, Flow Items could include actions such as "Remove this person from all groups" and "Disable all accounts belonging to this person."
Flow Items contain several parameters that collectively form a directive for the system. These parameters define the action, the target, and the scope of resources affected:
Item Type Action – Specifies the exact task to be executed. For example, “Bulk Remove Person Group Membership” might be an Item Type Action assigned to a Flow Item, directing the system to remove a person from multiple group memberships.
Item Type Scope – Determines the range within which the Item Type Action will execute. For instance, “Remove All Non-RBAC Group Accounts for Person” could be an Item Scope Type, meaning the “Bulk Remove Person Group Membership” action would apply to all group accounts associated with a person not managed by Role-Based Access Control (RBAC).
Item Collection Query – An SQL statement that retrieves specific resource data related to the Flow Item. For example, in a Flow Item labeled "Disable All Person Accounts" with an Item Scope Type of "All Accounts for Person," the query retrieves all accounts owned by the individual who is the subject of the Flow Item.
In effect, the Flow Item, the Item Type Action, the Item Scope Type, and the Item Collection Query collectively form an instruction for the system. They define what action to take, where to apply it, and the scope of resources it should impact. Administrators can construct complex, automated workflows that respond effectively to various Flow Events by stringing together multiple Flow Items within a Flow Definition.
EmpowerID includes several predefined Flow Items.
View Default Flow Items
| Flow Item | Description |
|---|---|
| Remove Non-RBAC Assigned group memberships from person | Remove Non-RBAC Assigned group memberships from the person who is a target of the item. |
| Disable Person | Disable Person account for the person who is a target of the item. |
| Just in Time Person Access Summary Recertification | Just in Time Person Access Summary Recertification for the person who is a target of the item. |
| Email a Person | Emails the Person who is the target of the item. |
| Email a Person's Manager | Emails the Person’s Manager who is the target of the item. |
| Disable Mailbox | Disable mailbox. |
| Disable All Person Accounts | Delete all accounts owned by the Person who is the target of the item. |
| Enable Person | Enable the Person who is the target of the item. |
| Restore Person | Restore the Person account who is the target of the item. |
| EnableOutOfOffice | Enables Out Of Office for the Person account who is the target of the item. |
| Remove Person Group Membership | Removes Person from group membership. |
| DisableOutOfOffice | Disables Out Of Office for the Person account who is the target of the item. |
| HideInGAL | Hides mailbox in GAL. |
| ShowMailboxInGAL | Shows mailbox in GAL. |
| EnableAllPersonAccounts | Enables all Person accounts. |
| EditAccountAttribute | Edit account attribute. |
Think of a Flow Definition as a set of instructions. It is a container that holds one or more Flow Items, which are steps the system follows to react to a particular event. Flow Definitions serve as templates for business processes, outlining how Flow Items are orchestrated in response to a specific Flow Event.
For example, a "Person Leaver" event could trigger actions such as disabling accounts and removing the person from all groups.
View Default Flow Definitions
| Flow Definition | Description |
|---|---|
| Person Leaver | Defines the Flow Items to be executed when a Person Leaver event occurs. |
| Person Mover | Defines the Flow Items to be executed when a Person Mover event occurs. |
| Person Rehire | Defines the Flow Items to be executed when a Person Rehire event occurs. |
The No Code Flows framework of EmpowerID operates through a central mechanism known as Flow Policies. These policies act as a bridge between specific events and their corresponding automated responses, facilitated by Flow Definitions. As the core rule set for No Code Flows, Flow Policies determine which Flow Definitions to trigger in response to certain Flow Events.
Flow Policies also allow multiple rules for a single event, enabling adaptability to changing organizational needs. For example, a company might have distinct procedures for handling internal employee departures versus external consultant contract terminations.
In such cases, separate Flow Policies can be established. An "Internal Departures" policy might disable access to internal systems, while a policy for "External Departures" could revoke temporary access permissions.
Additional Concepts
Beyond Flow Events, Flow Items, Flow Definitions, and Flow Policies, the No Code Flows framework also includes key concepts that govern how requests are initiated, processed, and fulfilled.
- Business Requests
- Business Request Items
- Approval Flow Policies
- Fulfillment Workflows
A Business Request is generated when an event triggers a Flow Definition. It represents a formal request to execute the actions defined in the definition.
Business Request Items are the individual tasks or actions that need to be executed as part of a Business Request. They are generated based on the Flow Definition and contain data such as request details, assignee ID, and resource ID.
Each item is processed independently, following the defined order in the flow. Items at the beginning are executed first, while dependent items wait for prerequisite tasks to complete.
Approval Flow Policies in EmpowerID define how Business Requests are routed to approvers. These policies ensure that requests are handled efficiently and in alignment with organizational approval structures.
For example, if a person updates their location within the organization, the request could be automatically sent to their manager for approval before any new resources are allocated. Approval Flow Policies allow for flexible handling of requests—some may require explicit approval, others may be auto-approved based on predefined rules, and certain scenarios, such as a person leaving the organization, may bypass approval altogether.
When a Business Request is linked to an Approval Flow Policy, the system determines the appropriate approval workflow based on the policy configuration. This enables organizations to implement structured and automated approval processes that align with their internal governance and compliance requirements.
Fulfillment Workflows outline the process for handling request items once approved, auto-approved, or rejected. These workflows execute actions based on the Approval Flow outcome.
Depending on the decision, different workflow branches may be triggered to update systems, notify stakeholders, or perform post-decision activities.
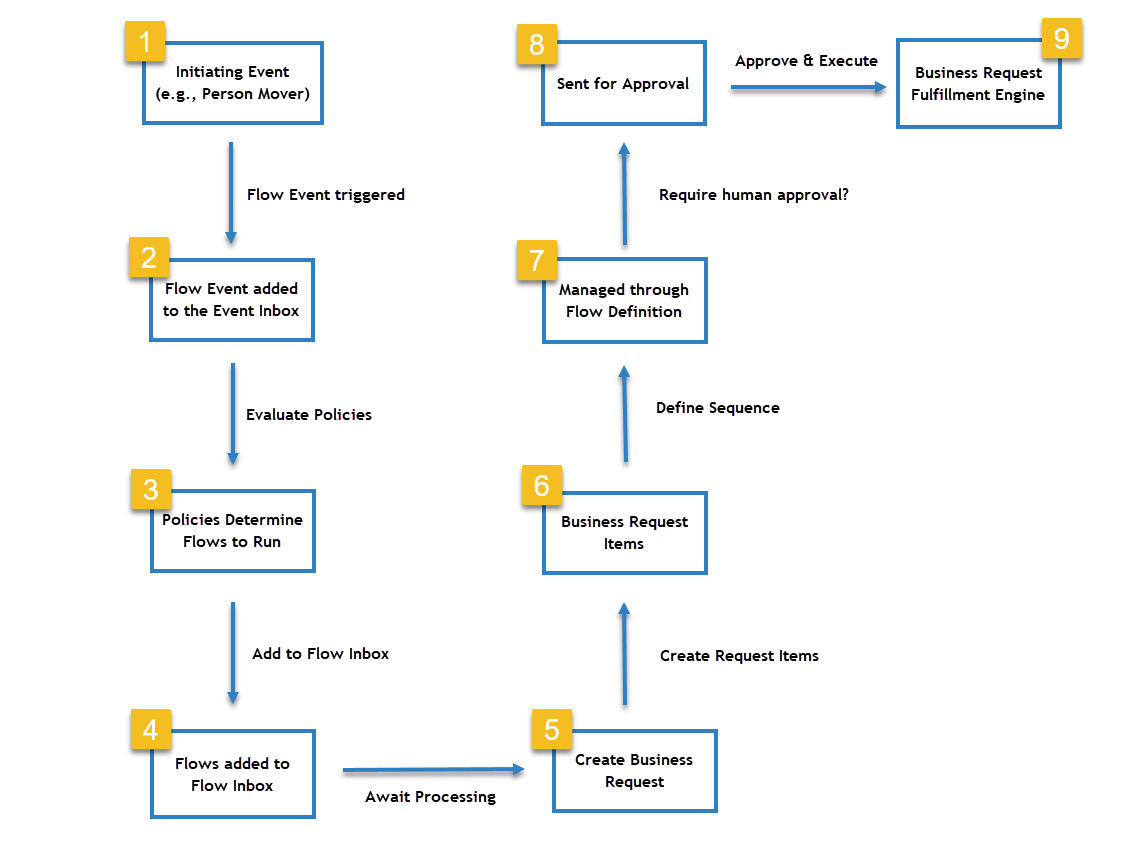
A Typical No Code Flow Execution Process
The Flow execution process in a No Code Flow involves the following steps. A graphical representation of the process follows the steps.
-
The flow initiates with an event, such as Person Mover.
-
The event is added to the Event Inbox.
-
The applicable policies determine the flows that need to be run. These flows are then added to the Flow Inbox.
-
Once in the Flow Inbox, each flow awaits processing.
-
Upon processing, each flow creates a Business Request. This request consists of multiple Business Request Items, which are individual tasks to be performed.
-
Each Business Request Item represents an action to be performed. This could range from adding the resource to a group to disabling the resource.
-
The sequence and timing of the Business Request Items are managed through the Flow Definition.
-
Items requiring human approval are sent for approval.
-
Upon human or system automated approval, each Business Request Item is sent to the Business Request Fulfillment Engine, which executes the tasks, fulfilling the requests.
Seamless Automation with No Code Flows
EmpowerID’s No Code Flows framework enables organizations to automate and orchestrate business processes efficiently by integrating Flow Events, Flow Items, Flow Definitions, and Flow Policies into a unified system.
Flow Events act as the initial triggers, capturing key business scenarios such as employee onboarding or account deactivation. These events drive Flow Definitions, which outline the sequence of Flow Items—specific actions like disabling accounts or modifying permissions—that must be executed in response.
At the core of this orchestration are Flow Policies, which define the overarching rules that govern process execution. Flow Policies determine which Flow Definitions should be triggered in response to a given Flow Event, allowing for customization based on organizational requirements. By configuring multiple policies for different scenarios—such as handling internal employee departures versus external consultant contract terminations—organizations can tailor automated workflows to align with their security, compliance, and operational policies.
This modular and scalable approach ensures that every business event is processed consistently and efficiently, reducing manual intervention while maintaining flexibility. By leveraging these interconnected components, organizations can construct custom workflows that adapt to evolving business needs, reinforcing the principles of automation, security, and process optimization.